Everything in the world has its own pros and cons. Even though the best of the developers think of the possible uses of a technology, one can never restrict usage of it.
Technology has managed to prioritize on major facet of our lives and that is Time. The time consumption for any basic task has decreased by a major percentage over the couple of decades. Also it has made the availability of resources at the finger tips enabling a person to multi task thereby increasing the productivity levels too.
The transition of technology in this process began with the concept for “work-from-anywhere”. Organisations couldn’t let go of the opportunity of monetizing technology’s boon of resource availability anywhere and everywhere. At the other end people loved to improve their productivity quotients with ease when they thought idle time could be out to use the smartest way.
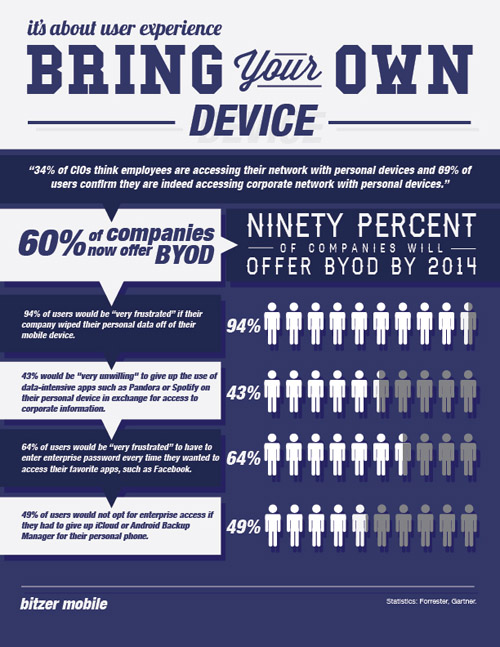
The above was followed by era of using the “smartness” of handheld devices at the work front to enhance performance. BYOD came in at this stage. BYOD , as most of us know, stands for, Bring Your Own Device. Many organizations embraced this technology gracefully but many questioned the liberty. Data security, which is the biggest challenge today in the field of technology, was at stake.
Although it’s trendy, fad and classy, it’s dangerous. Companies’ IR departments clearly mentioned to the management that if the management demanded data security, they had to be allowed to control personal smartphones and tablets. They demanded employees to be required to use corporate-issued management and security software to monitor or remote wipe.
Mobile device management software and services came into the picture at this junction. Some of them available today are :
- FiberLink MaaS360
- GroupLogic for secure file-sharing
- Mobile Iron
- AirWatch mobile management software
- SonicWall Aventail EX 6000 VPN access to agency data